Nginx服务安全加固
1、禁止频繁访问的ip访问nginx
生产环境中经常会遇到某个ip地址频繁异常的访问nginx网站,此时我们需要通过安全措施保护我们的服务器
部署nginx
[root@localhost tools]# yum install gcc gcc-c++ make automake autoconf libtool pcre* zlib openssl openssl-devel[root@localhost tools]# tar xf nginx-1.11.2.tar.gz[root@localhost tools]# lsnginx-1.11.2 nginx-1.11.2.tar.gz[root@localhost tools]# cd nginx-1.11.2[root@localhost nginx-1.11.2]# lsauto CHANGES CHANGES.ru conf configure contrib html LICENSE man README src[root@localhost nginx-1.11.2]# ./configure[root@localhost nginx-1.11.2]# make[root@localhost nginx-1.11.2]# make install
测试nginx服务
[root@localhost ~]# curl -I 172.16.1.100HTTP/1.1 200 OKServer: nginx/1.11.2Date: Mon, 17 Aug 2020 09:36:29 GMTContent-Type: text/htmlContent-Length: 15Last-Modified: Mon, 17 Aug 2020 09:36:19 GMTConnection: keep-aliveETag: "5f3a4f93-f"Accept-Ranges: bytes
nginx 可以正常访问。
接下来,假设172.16.1.100是黑客主机,频繁访问nginx服务
模拟172.16.1.100访问10次172.16.1.10
172.16.1.100
[root@localhost ~]# ab -c 1 -n 10 http://172.16.1.10/This is ApacheBench, Version 2.3 <$Revision: 1430300 $>Copyright 1996 Adam Twiss, Zeus Technology Ltd, http://www.zeustech.net/Licensed to The Apache Software Foundation, http://www.apache.org/Benchmarking 172.16.1.10 (be patient).....doneServer Software: nginx/1.11.2Server Hostname: 172.16.1.10Server Port: 80Document Path: /Document Length: 612 bytesConcurrency Level: 1Time taken for tests: 0.016 secondsComplete requests: 10Failed requests: 0Write errors: 0Total transferred: 8450 bytesHTML transferred: 6120 bytesRequests per second: 617.02 [#/sec] (mean)Time per request: 1.621 [ms] (mean)Time per request: 1.621 [ms] (mean, across all concurrent requests)Transfer rate: 509.16 [Kbytes/sec] receivedConnection Times (ms)min mean[+/-sd] median maxConnect: 0 1 0.3 0 1Processing: 1 1 0.3 1 2Waiting: 0 1 0.3 1 1Total: 1 1 0.5 1 2ERROR: The median and mean for the initial connection time are more than twice the standarddeviation apart. These results are NOT reliable.Percentage of the requests served within a certain time (ms)50% 166% 175% 180% 290% 295% 298% 299% 2100% 2 (longest request)
查看nginx日志
172.16.1.10
[root@localhost ~]# tail /usr/local/nginx/logs/access.log172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"172.16.1.100 - - [26/Jul/2020:05:58:24 +0800] "GET / HTTP/1.0" 200 612 "-" "ApacheBench/2.3"
由此可见,一秒钟之内172.16.1.100访问了nginx10次,接下来禁止掉这个问题ip
通过iptables限制ip访问
172.16.1.10
[root@localhost ~]# iptables -I INPUT -s 172.16.1.100 -ptcp --dport 80 -j DROP
172.16.1.100
[root@localhost ~]# curl 172.16.1.10curl: (7) Failed connect to 172.16.1.10:80; 连接超时
此时172.16.1.100再也不能访问nginx
nginx配置文件限制
172.16.1.10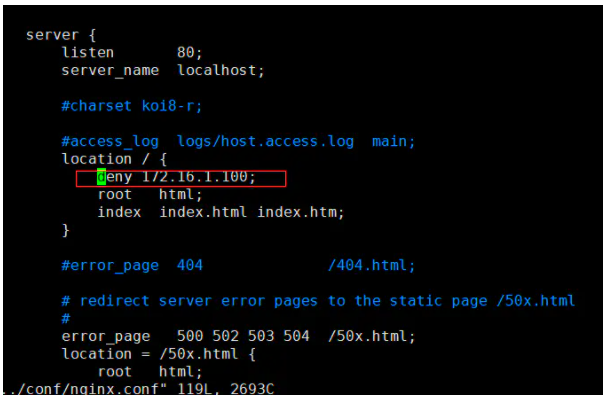
172.16.1.100
[root@localhost ~]# curl -I 172.16.1.10HTTP/1.1 403 ForbiddenServer: nginx/1.11.2Date: Sat, 25 Jul 2020 23:12:06 GMTContent-Type: text/htmlContent-Length: 169Connection: keep-alive
总结
以上就是两种简单的方法限制ip访问,还有许多方法可以利用工具进行ip限制。
参考链接 :
禁止频繁访问的ip访问nginx :https://www.jianshu.com/p/48a8bbeaf76a





























还没有评论,来说两句吧...